Each test generates detailed reports for IT and security teams, with precise guidance on how to act and strengthen the defensive posture.
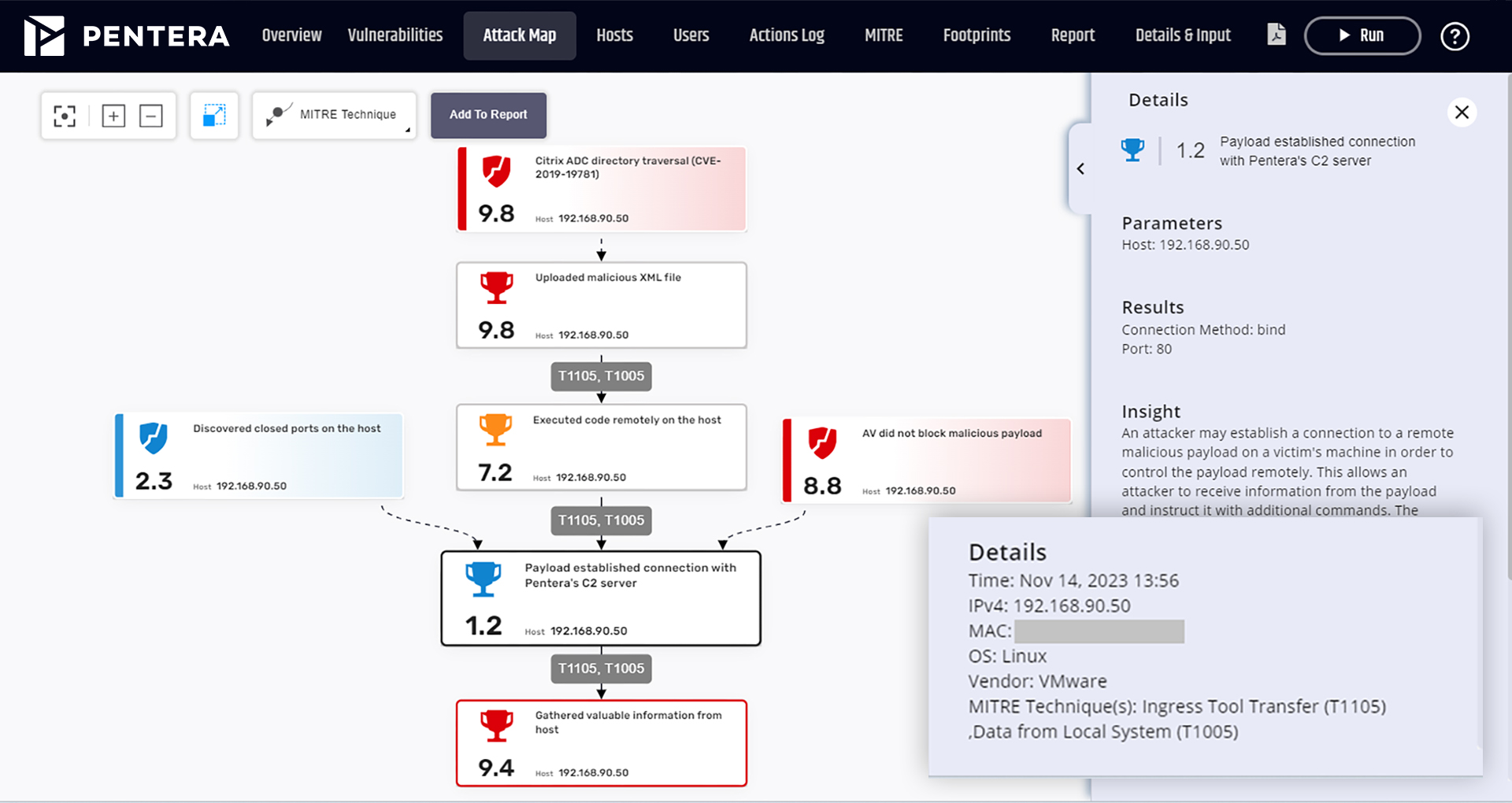
The platform that performs real penetration tests continuously and fully automatically.
Automated Penetration Testing
Pentera’s Automated Penetration Testing platform allows realistic simulations of cyber attacks within the corporate infrastructure, safely, quickly, and at scale, without human intervention. Through our partnership with Pentera, we offer a cutting-edge solution to test the effectiveness of your company’s cyber defenses in real time, providing detailed, actionable reports.
How does it work?
Continuous simulation of real attacks
Pentera emulates techniques used by real attackers, testing the corporate network from the inside as a threat actor would, without impacting operations.
Fully automated penetration testing
This is not a vulnerability scan, but a full penetration test—fully automated and performed whenever needed.
Prioritization of actual risks
Identifies only the vulnerabilities that can actually be exploited, excluding false positives. Provides a clear view of business impacts.
Immediate technical and operational report
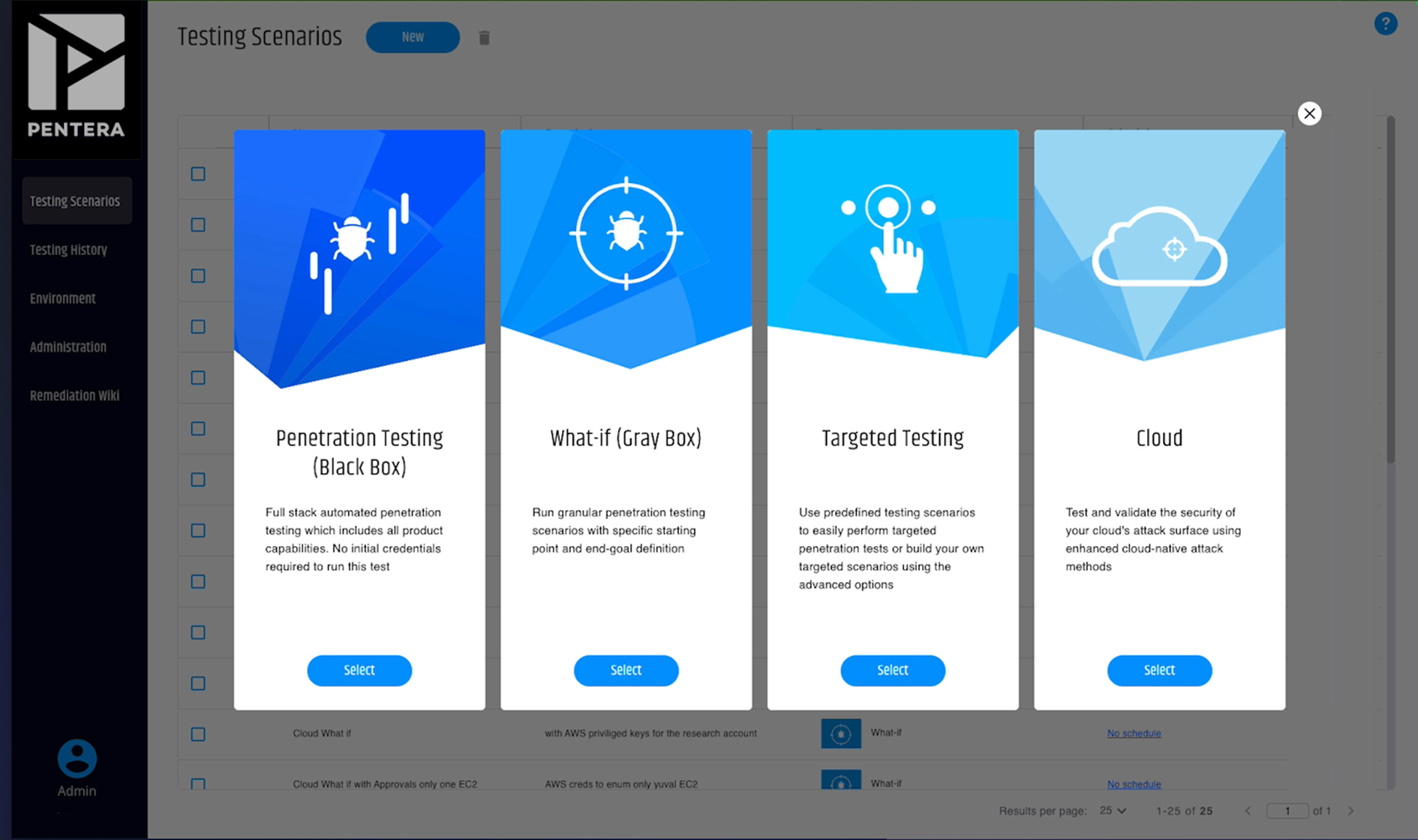
The benefits of choosing the Pentera solution
Improve your security posture in a measurable way
Eliminate security gaps before they can be exploited
Test your network with real attacks, not just theoretical simulations
Automate remediation and defense updates
Clear visibility for CISO, IT Managers, and the Board
Ensures compliance (NIS2, ISO 27001, DORA)
Test. Improve. Repeat. With Pentera.
Our partnership
We are official Pentera partners, with specialized expertise in security validation, remediation, and threat management.
We support you through every phase: initial deployment, customization of attack scenarios, interpretation of results, and addressing the most critical vulnerabilities.
FAQ

Does Pentera simulate advanced attacks?
Yes. Pentera supports complex attack scenarios such as Lateral Movement, Privilege Escalation, Active Directory Exploitation, Credential Dumping, and Data Exfiltration Simulation. These tests reflect the real techniques used by attackers and help identify vulnerabilities that can actually be exploited.
Is Pentera safe to use in production environments?
Absolutely. Pentera performs exploits in a controlled, agentless manner, without interrupting services or compromising the infrastructure. All activities are designed to be non-destructive, ensuring the safety of the production environment.
How are the tests performed documented?
Each validation activity includes detailed logs, technical evidence, and remediation suggestions. This allows IT and security teams to take targeted action, improve the security posture, and close security gaps in a structured and verifiable way.
Does Pentera also cover cloud environments and web applications?
ChatGPT ha detto:
Yes. The platform includes tests on web application exploitation and analyzes misconfigurations in the cloud (cloud misconfiguration abuse). It validates the effectiveness of security measures on hybrid infrastructures in real time.
Is it necessary to install an agent or modify the infrastructure?
No. Pentera operates in an agentless mode: it does not require software installation on endpoints. This simplifies adoption and allows rapid integration into your security processes.

